Getting into the Hacking World is exciting and luring for sure. There are lots of shows out there that have made Hacking look appealing, and rightly so! To learn how the very environment that your technical life is built on is extremely useful. Not only to help you better understand how everything works, but also to better protect yourself from making mistakes that might cost you in the end.
What Is Hacking?
Believe it or not, it involves more than drinking coffee and wearing hoodies… It also involves being wrong…… ALL. THE. TIME. But what separates a Hacker from a typical PC User is that they keep trying different ways to get a result. If one way doesn’t work, they gain a bit of knowledge and use that for their next attempt. Once they learn how a system works, they can better exploit it.
Black Hat
The black hat hacker is the one who hacks for malicious intent. This is the guy who is going to hack your camera, steal your credit card, get into your homes security system. What is the intent? Just to do damage, Personal Gain, Disrupt your Life in some way. He is also labeled Black hat in the sense that he DOES NOT have permission from the owner of the device he is exploiting to do what he is doing.
White Hat
This white hat hacker is someone who is usually working for a company or defense organization. They are the ones who are working offense, are up to speed on all the methods used by the Black Hats, but use it in an ethical way. They can be teachers, or just be behind the scenes. (Hoodie Optional)
Grey Hat
These guys are more like white hat hackers than anything else. Their methods of going about doing some of their testing or some of their work in general can be question able and may violate laws at times. However, they are never in a position to do malicious damage like a black hat hacker.
I Am Intrigued… Where Do I Start?
There are lots of ways to start learning your way around networks and security systems. The easiest way and cheapest (Free!) is the way I will explain here. First you will need a computer. (Obvious, but has to be said). You will need a Linux based operating system and lastly, you will need some devices to practice hacking.
Linux Flavor
Though attempting to learn how to do some pentesting in windows is possible, it is not advisable. There are lots of free Operating systems per-configured with all the tools you will need to get your foot in the door to the hacking world. I will only highlight the two I use regularly…
1. Kali Linux – Kali Linux is an open source project that is maintained and funded by Offensive Security, a provider of world-class information security training and penetration testing services.
2. ParrotOS – (Parrot Security, ParrotOS) is a free and open source GNU/Linux distribution based on Debian Testing designed for security experts, developers and privacy aware people.
Once you have downloaded and installed it into a Virtual Environment or to a dedicated machine, we can get started with HTB.
Hack The Box
Hack the Box is a community where virtual machines are submitted by security experts as well as security enthusiasts and hosted for people to attempt to gain access.
These machines are available to the community to test their skills in gaining access. Once a machine is compromised, there is a file located on the Users Desktop that has a string of code in it. Once the pentester has gained access to the machine, he or she will paste it into the space provided to prove that access was gained to the computer.
There is also another file located on the admin desktop or root of the machine. This also contains a string of letters and numbers. Gaining access to admin or root is usually much more difficult and requires know how on elevating privileges. Once a user puts both codes in, the machine is considered owned by the user.
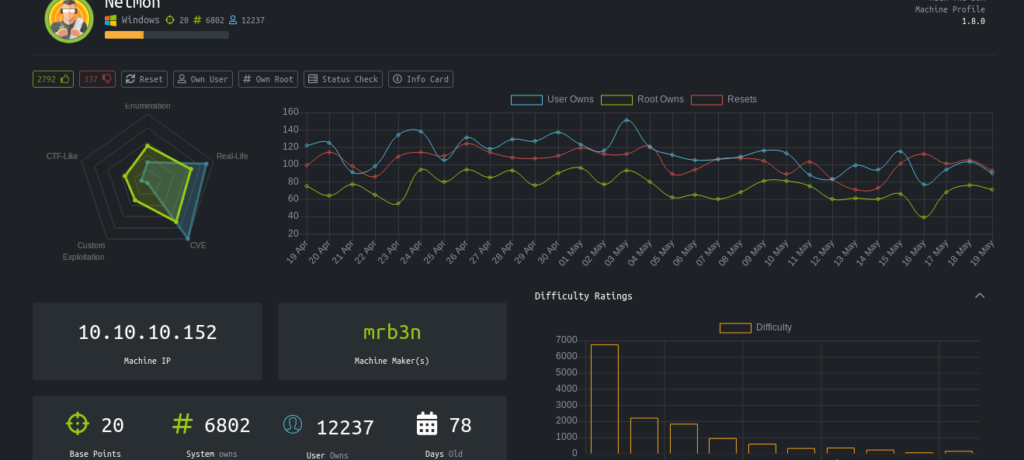
Stats and reviews are provided to help users get an idea if the machine is within their skill set. Start by creating a username and password… Wait…. You can’t. You have to hack that process as well! No worries, there are tutorials out there to help you. It does help to get your foot in the door and follow a tutorial, especially if you have never stepped over into this kind of territory before. Once in and an account has been created, you will be able to start out on an easy machine and get a taste of what the hacking process is like.
Tools of the Trade
- Metasploit : The world’s most used penetration testing framework
- Armitage: Graphical User Interface for the Metasploit Framework
- Nmap: Free Security Scanner, Port Scanner, & Network Exploration Tool.
- Exploit DB: A collection of Exploits used in Metasploit as well as submissions by users to exploit known vulnerabilities.
- CVE: A complete database of security vulnerabilities currently known. Includes detailed explanations of patches as well as exploits used.
With these basic tools you can get a few of the easiest machines on Hack The Box. It is not going to be easy going for your first try. It took me at least 3 weeks to get my first machine and even longer for my second. However, each day you spend attempting to gain access you are learning more than you could ever know. Things that failed in getting you into one machine may be what you need to gain access to others. The point I am trying to say is… Keep Trying! Don’t Give Up!
Of course, if you are wanting to get your company online, but don’t have the time to worry about security, rest easy! Our security team here at 4Site can ensure that your website is secured from intrusion. Not only do we do this for work….It’s kinda our hobby!
Have your own set of tools that you can’t live without? Leave them in the comments below!



![[Solved] How To Install Exploit-db (Searchsploit) On Ubuntu 19](https://4siteadvantage.com/wp-content/uploads/2020/04/ExploitDB-Banner.png)
![[Solved] Katoolin for Ubuntu 20.04](https://4siteadvantage.com/wp-content/uploads/2020/02/Screenshot-from-2020-02-17-09-40-07-400x156.png)
0 Comments